CAN Frame Decoding
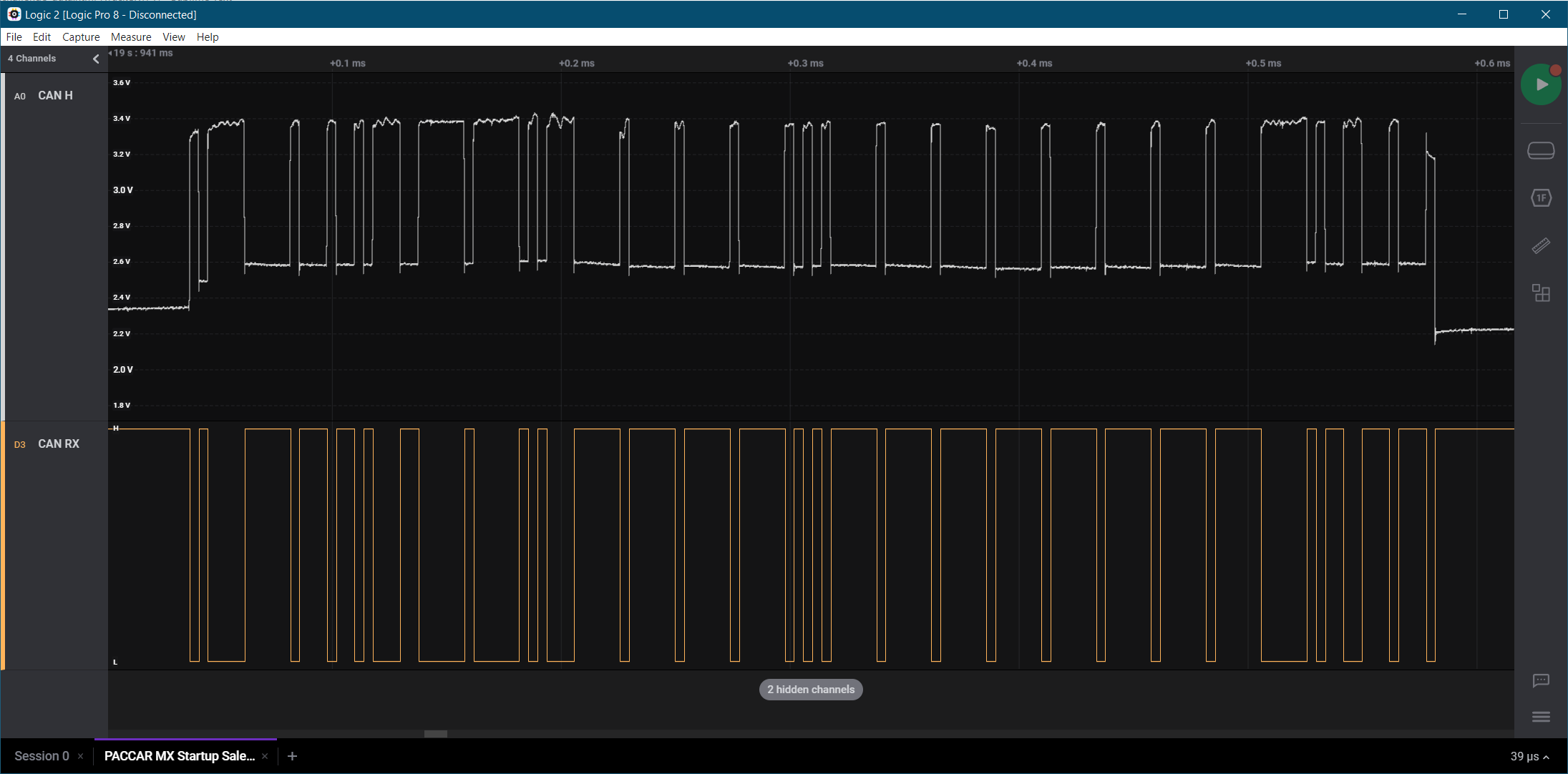
A CAN stream was captured from a PACCAR MX engine communicating at 250,000 bits/second on a J1939 network. Two signals were captured: 1) the analog voltage for the CANH signal line (pin C of the 9-pin diagnostic connector) and 2) the digital signal from the CAN RX pin of the CAN transceiver. Each file is available as a comma separated value (CSV) file:
Analog Trace (621KB)
Digital Trace (1KB)
The traces were exported from the Saleae Logic program. The analog trace has observed values at 50MHz and the digital trace provides a list of the times where each transition takes place.
Challenge Questions
- What is the priority of the message?
- What is the parameter group number?
- What is the destination address?
- What is the source address?
- What is the length of the data?
Seed-Key Exchange
Middle Machine Attack
A candump data log was capture during a diagnosic session using Linux SocketCAN. The data comes from a J1939 network that contained a couple ECUs and a diagnostics adapter. A man-in-the-middle was inserted between the main J1939 and an ECU. The man in the middle can change message traffic as it is passing it from one side of the MITM to the other. In this file, there was only an attack on 1 message. The challenge is to determine the following based on the data in this log file:
- What was PGN of the attack?
- Which ECU was the subject of the attack?
- What data was changed?
Signal Interpretation
A candump data log was capture during a startup seqence for a truck using Linux SocketCAN. The data comes from 2014 Class 6 truck with a box van where the operator started the engine, pressed the accelerator pedal and turned the engine off. The challenge is to determine the highest engine speed in RPM base on the log file.
Some other questions for consideration:- How many ECUs are on the network?
- What is the vehicle mileage?
- Did the vehicle's wheels rotate?